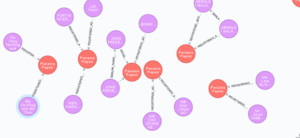
On of the most interesting and important projects reported on at the 33c3 was the Syrian Archive project. This is an immensely important project that is impart documenting the Syrian conflict, including the human cost, but is also trying to help work towards a lasting peace in Syria. A major component of this work involves the curation of documentary evidence.
This includes evidence gathering and documentation of incidents; the acknowledgement that war crimes and human rights violations have been committed by all sides; the identification of perpetrators to end the cycle of impunity and the development of a process of justice and reconciliation.
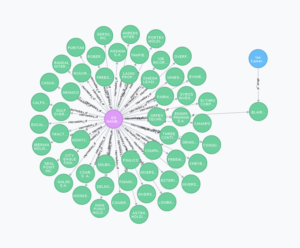
The project which started in 2014 collects data, often in the form of images or video, from citizen journalists on the ground in Syria. The goal being to create an evidence based tool that can be used by journalists, HRDs and lawyers. The collected data is then securely stored on backed up servers, reducing the potential for loss of evidence. The project also builds meta-data for the evidence, which is often lost (particularly if the video is uploaded to social media services which often strip out the meta-data). Meta-data is often extremely important for the verification of the evidence as it helps to locate an incident temporally and spatially.
They also work to ensure the integrity of the data, including by producing a hash code of the data at the point of upload. This ensures that the evidence cannot be tampered with at some later point. All this is done through a range of simple tools. The result is a verifiable, searchable, and secure data repository that is accessible to anyone. The archive also allows for evidence to be cross referenced across multiple sources, and multiple platforms, helping to verify the claims.
This work is of great value as often in wars all sides seek to hide the full extent of their impact on the civilian population. The database has already proved instrumental in determining the facts around an air strike that wrongly hit a Mosque in Syria. Claims and counter claims cast doubt of the real events, with the Russian ministry of defence claiming that the Mosque was still intact, but witnesses claiming it had been destroyed. The data set allowed investigators to verify that a Mosque had been hit, and only that the name of the Mosque was incorrectly reported, leading to the confusion. Both the actual incident, and the claimed incident, can both be recorded in the database. The archive also allows the use of tactics or weapons to be tracked across multiple events, such as the use of chemical weapons.
The openness is key to this project, and links with some of my own research. We live in a world where different interested parties will make claims and counter claims about news or events. This makes it hard to determine which claim is best supported by the evidence on the ground. What this archive, and others like it, do is allow anyone to make an assessment of the evidence available, perhaps enabling them to understand the events in question better.
The talk was presented by Jeff Deutch and Hadi Al-Khatib, thanks to them for letting look at the slides again for reference. The videoed talk is linked below.